Cybersecurity at the Department of Energy’s Oak Ridge Leadership Computing Facility is under constant pressure from millions of unauthorized connection attempts each day. Now, a major upgrade to the facility’s monitoring system has strengthened defenses, reinforcing one of the nation’s most powerful computing resources against hidden threats.
To address this challenge, the OLCF, a DOE Office of Science user facility at Oak Ridge National Laboratory, has upgraded its Network Intrusion Detection System, or NIDS. This system enhancement, which required two years of careful planning and execution, has significantly strengthened the OLCF’s ability to monitor and secure network traffic. By protecting critical research and safeguarding sensitive data, these advancements ensure the continued reliability of high-performance computing, which drives breakthroughs in science, energy innovation, and national security.
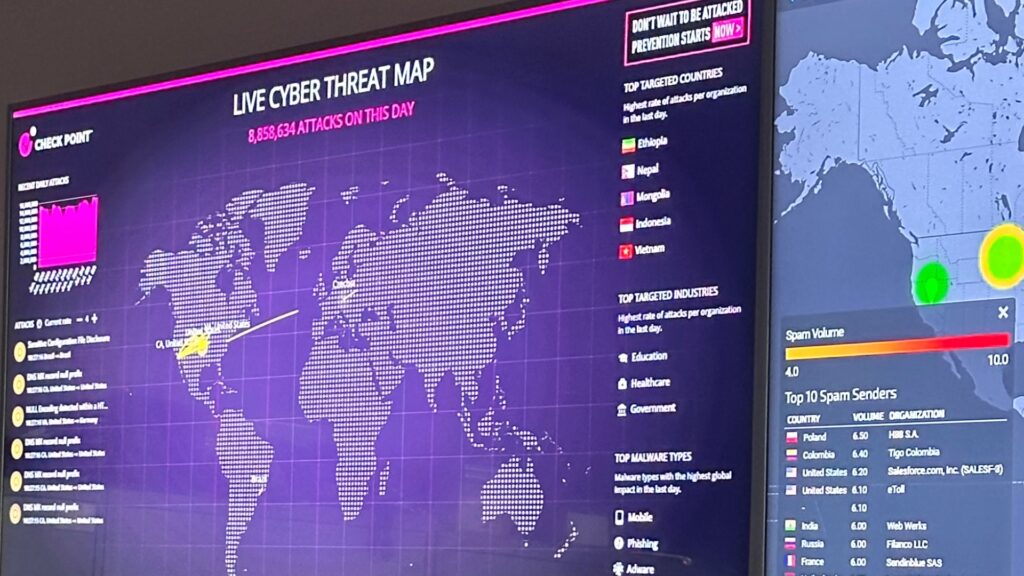
A cyber threat map is displayed inside the Security Operations Center at Oak Ridge National Laboratory.
Completed in April 2025, the project was driven by needs to meet security accreditation requirements and to adapt NIDS to an upgraded network infrastructure. The previous system became inadequate due to advancements in networking technology, which created a need for a new approach capable of efficiently managing larger volumes of data.
The project was led by Ryan Adamson, group leader for HPC Cybersecurity, along with HPC system administrator Jakob Becklehimer and HPC cybersecurity engineer Carl Bai. The team collaborated with the OLCF’s HPC Networking team to bring the project to completion.
NIDS can now process traffic at speeds of up to 400 gigabits per second, four times faster than its former 100 Gbps specification. This quadrupling of capacity not only enhances the OLCF’s ability to track potential intrusions but also ensures a secure environment for conducting scientific research.
“Essentially, we now have the capability to view and verify any and all traffic entering or exiting the supercomputing enclave,” Becklehimer said.
With the NIDS upgrade, system analysts can clearly see patterns in web traffic and differentiate between traffic that’s coming from web browsers, scientific data transfers or system services. The new capabilities enable analysts to pinpoint differences or changes in traffic while providing a breakdown of information, including who the users are and where the traffic is going. Data being transferred to countries where it wouldn’t be expected to go is flagged, and the sizes of the data flows are reported.
“We would expect to see large data transfers for scientific datasets,” Adamson said. “We wouldn’t expect to see data transfers for sensitive datasets that the facility might have. This slices and dices the internet traffic and gives a view of that so we understand the state of the network.”
Upgrading Defenses to Support Critical Research
Throughout the project, the HPC Cybersecurity team faced various challenges, including delays with hardware shipments and compatibility issues with existing equipment. Despite these hurdles, collaboration between system administrators and the HPC Networking team enabled the successful installation and configuration of the new system. The project was completed using open-source software tools that enhance network security so that the NIDS upgrade strengthens the organization’s defenses against potential threats and simultaneously supports the collaborative spirit of the scientific community.
NIDS now includes upgraded worker nodes, meaning that the servers running the NIDS software are much more powerful than the previous ones. Also included are a network aggregation switch and passive test access points, which provide a comprehensive solution for monitoring traffic without affecting the user experience. The passive network test access points are located throughout the main entry and exit points of the network, so when the traffic comes in, there is now a separate line that passively comes out. The passive lines from the test access points branch off the entry and exit points so that everything can be monitored without all the traffic that flows through these entry and exit points being directly affected.
“Our monitoring is totally passive, so users won’t notice any difference,” Becklehimer said. “We are constantly aware of the traffic patterns and can respond to threats as they arise with tools that allow us to block malicious activity almost automatically.”
In addition to boosting immediate security capabilities, the new system positions the OLCF to address future challenges. The scalable design of NIDS is a key factor because the current OLCF infrastructure is set to accommodate future demands, particularly as collaborations with strategic partners such as the U.S. Air Force expand.
The current NIDS system is projected to last approximately seven years before needing another refresh.
“Security is never a one-time solution — it’s an ongoing process. We’re already preparing for additional upgrades to adapt to upcoming networking changes,” said Ryan Adamson, group leader for HPC Security.
Aligned with DOE’s mission priorities, the NIDS upgrade marks a pivotal step in ensuring the integrity of ORNL’s cybersecurity measures. The upgrade will help the OLCF safeguard its vital scientific computing and collaboration while and adapt to future challenges.
“Protecting datasets from world-leading scientific campaigns is crucial for enhancing the efficiency of our operations and ensuring that we make the most of taxpayer dollars,” Adamson said. “We’re committed to conducting our research responsibly and effectively while minimizing redundancy and avoiding unnecessary expenditures.”
UT-Battelle manages ORNL for the DOE’s Office of Science, the largest supporter of basic research in the physical sciences in the United States. The Office of Science is working to address some of the most pressing challenges of our time. For more information, visit energy.gov/science.